Using SSL/TLS with Relativity
Version Note: This article describes the new TLS/SSL support in Relativity Server 9 and later. For using SSL with Relativity 8 or below please see here.
Setting up the Transport-Level Security (TLS) in Relativity Server is very easy in version 9.0 and later. There are three simple stops involved:
- Provide a TLS/SSL certificate to the Relativity Server
- Make sure that it was accepted by the server
- Enable TLS/SSL on the server channel
1. Provide a TLS/SSL Certificate
Relativity Server will automatically load any certificate found in a file named Relativity.p12 located in the Relativity Server's configuration folder.
Alternatively to manually placing this file, the Relativity Admin Tool allows you to either upload a local certificate file, or to have a self-signed certificate generate by the server:
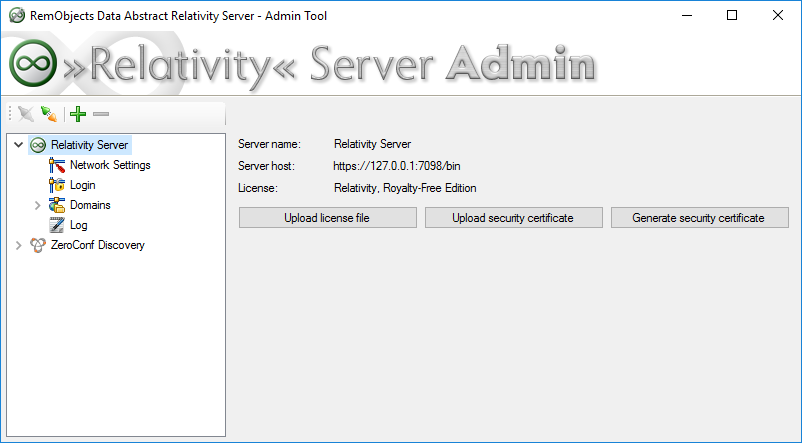
This certificate file (whether uploaded, or manually placed on the server) should be a PKCS#12 certificate file without password.
Please note that by default some client OS (such as iOS or Windows Phone) will reject the self-signed certificates by default. You may need to manually register the certificate on the client, or you may neeed to add extra code to your client application to approve the certificate. See here for more information.
2. Make sure that it was accepted by the server
To make sure everything is working, open your web browser and go to the address of your Relativity server on port 7098 (e.g. https://localhost:7098). If the page opens correctly, then the security certificate was successfully found, uploaded or generated, and was accepred by the Relativity Server.
Enable TLS/SSL on the server channel
In Relativity Admin, go to the 'Network Settings' page. The channel types Http, SuperHttp, Tcp and SuperTcp now all expose a new option called "Enable TLS" (unfortunately due to the platform restrictions HttpSys and SuperHttpSys channels will need to use the old, IIS-based workflow):
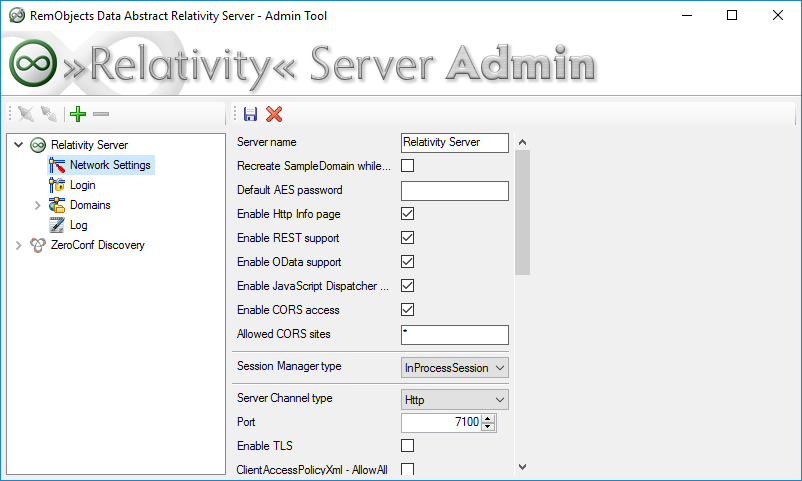
Enable the option and apply the changes, and your server should be all set for secure access.